Adobe ColdFusion Access Control Bypass Attack
Watch Video
Adobe ColdFusion Access Control Bypass Attack Video
Critical-level detections in the wild
FortiGuards labs observed extremely widespread exploitation attempts relating to security bypass vulnerabilities in Adobe ColdFusion. Successful exploitation could result in access of the ColdFusion Administrator endpoints. Learn More »
Common Vulnerabilities and Exposures
Background
Adobe ColdFusion is a commercial rapid web-application development computing platform to rapidly build, test and deploy web applications. Previously, in Aug 2023, we saw it being actively targeted by the attackers to exploit CVE-2023-26359, CVE-2023-26360 which lead to the release of an Outbreak Alert at that time, to read the full Outbreak visit: https://www.fortiguard.com/outbreak-alert/adobe-coldfusion-code-execution
Threat Radar Overall Score: 4.4
| CVSS Rating | 9.0 | |
| FortiRecon Score | 90/100 | |
| Known Exploited | Yes | |
| Exploit Prediction Score | 97.2% | |
| FortiGuard Telemetry | 8390 |
Latest Development
Recent news and incidents related to cybersecurity threats encompassing various events such as data breaches, cyber-attacks, security incidents, and vulnerabilities discovered.
Jul 19, 2023: Adobe released security updates for ColdFusion versions 2023, 2021 and 2018 to fix (CVE-2023-38205).
https://helpx.adobe.com/security/products/coldfusion/apsb23-47.html
At the time of the release, Adobe mentioned that CVE-2023-38205 has been exploited in the wild and has been seen in limited attacks. Please note, CVE-2023-38205 was released as a fix for incomplete patch for CVE-2023-29398.
July 20, 2023: Adobe ColdFusion vulnerabilities (CVE-2023-38205, CVE-2023-29298) were added to CISA's KEV catalog.
Nov 28, 2023: CVE-2023-26347- Another Access Control Bypass vulnerability was announced and Adobe released patches for it.
https://helpx.adobe.com/ca/security/products/coldfusion/apsb23-52.html
Jan 8, 2024: CVE-2023-38203- Adobe ColdFusion Deserialization of Untrusted Data Vulnerability, was added to CISA KEV list and has been seen to be actively exploited.
Jan 2024, FortiGuard Labs observed critical level of continued attacks on Adobe Coldfusion with IPS detections reaching upto 50,000+ unique detections. Users of Adobe ColdFusion are advised to apply patches as per vendor guidelines as soon as possible to mitigate any risk completely, if not already done.
Attack Sequence
Actions taken by cyber attacker or a malicious entity to compromise a target system or network.
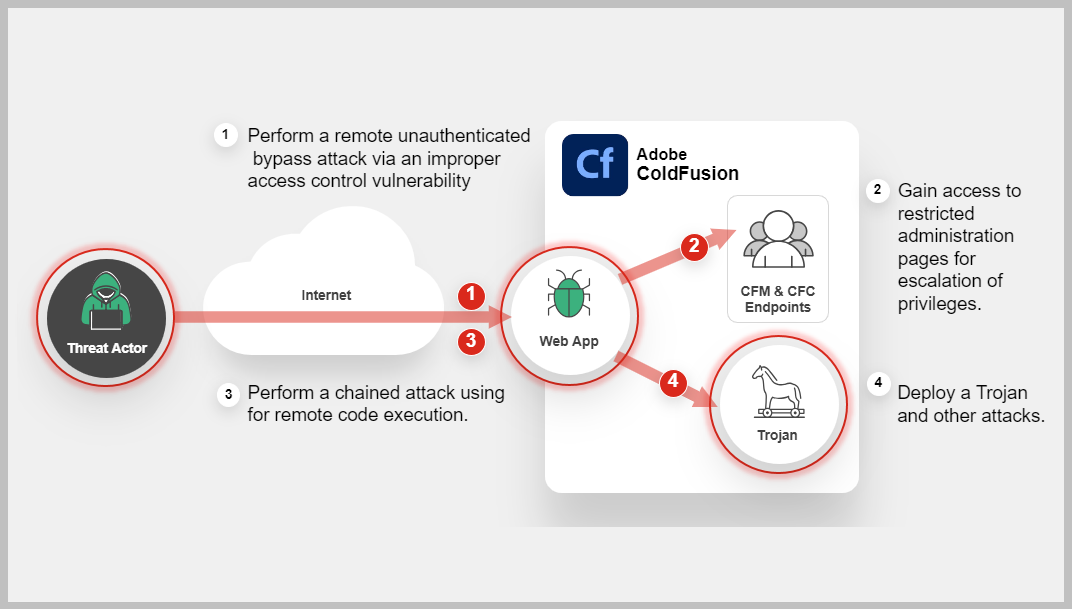
Attack Sequence

Attack Sequence Video
FortiGuard Cybersecurity Framework
Mitigate security threats and vulnerabilities by leveraging the range of FortiGuard Services.
-
Vulnerability
-
IPS
-
Web App Security
-
Outbreak Detection
-
Threat Hunting
-
Playbook
-
Assisted Response Services
-
Automated Response
-
NOC/SOC Training
-
End-User Training
-
Vulnerability Management
-
Attack Surface Hardening
-
Business Reputation
Vulnerability Detects vulnerable systems related to Adobe ColdFusion Bypass Attack
IPS Detect and block attack attempts targeting Adobe ColdFusion Access Control Bypass Attack
Web App Security Detect and block attack attempts targeting Adobe ColdFusion Access Control Bypass Attack
Outbreak Detection
Threat Hunting
Playbook
Assisted Response Services Experts to assist you with analysis, containment and response activities.
Automated Response Services that can automaticlly respond to this outbreak.
NOC/SOC Training Train your network and security professionals and optimize your incident response to stay on top of the cyberattacks.
End-User Training Raise security awareness to your employees that are continuously being targetted by phishing, drive-by download and other forms of cyberattacks.
Vulnerability Management Reduce the attack surface on software vulnerabilities via systematic and automated patching.
Attack Surface Hardening Check Security Fabric devices to build actionable configuration recommendations and key indicators.
Business Reputation Know attackers next move to protect against your business branding.
Threat Intelligence
Information gathered from analyzing ongoing cybersecurity events including threat actors, their tactics, techniques, and procedures (TTPs), indicators of compromise (IOCs), malware and related vulnerabilities.
Loading ...
 Indicators of compromise
Indicators of compromise
IOC Indicator List
 Indicators of compromise
Indicators of compromise
IOC Threat Activity
Last 30 days
Chg
Avg 0
Mitre Matrix

Click here for the ATT&CK Matrix
References
Sources of information in support and relation to this Outbreak and vendor.