Linux/Hinata.REAL!tr
 Analysis
Analysis
Linux/Hinata.REAL!tr is a generic detection for a trojan.
Since this is a generic detection, malware that are detected as Linux/Hinata.REAL!tr may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware is associated with the Realtek SDK outbreak and involves the CVE-2014-8361 vulnerability. The vulnerability is found in the miniigd SOAP service in Realtek SDK which allows arbitrary remote code execution by remote attackers.
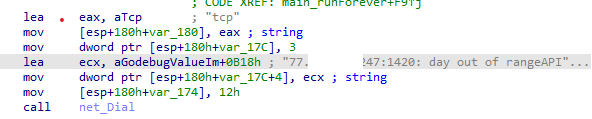
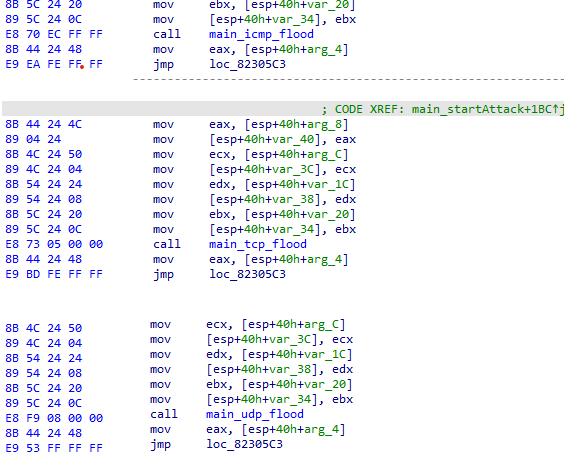
- Linux/Hinata.REAL!tr is a DDos botnet written in Go. It will attempt to gain access to a victim's system and wait for commands from the control server. The malware may perform malicious actions such as a distributed denial-of-service(DDoS) attacks.
- The botnet will attempt to connect to the following IP:
- 77.73[removed]247
- This malware has been associated with the following third party article/advisory.
https://nvd.nist.gov/vuln/detail/CVE-2014-8361 https://www.cvedetails.com/cve/CVE-2014-8361/

|
|
|
- Md5: 67fd38f84b11770cdd58040bd5686eb9
Sha256: 71067d5ae6fbede66cd1dd1f37fb191ee660b3363e3101dbdccb99284e03f660 - Md5: 171a6110335ad03e25485e7a821e458e
Sha256: a2f8dd1b6c39d11e80c0c8abea03aef7481e681ea0e04b97ca3306b423ff3da4 - Md5: ba2470126f4aa552d5bade243e60a15b
Sha256: f4b447d2f5cccde35d60edaedd97d089c9f1dc4630ffcd60317e9a0e2054a23b - Md5: c2c5ffaa6e343394dd9431c62c917611
Sha256: 5643bf01e113de246575a9ec39ea12a85f9babb6ac069132ad8d1a7bfa56ed1b - Md5: f6c73344f9d3632f4066cf9d837e2c98
Sha256: 4fe979cd35444a38398cd1595e804f01d70a7c0049b9ddebf345b4d26fe4c877
 Outbreak Alert
Outbreak Alert
FortiGuard Labs continue to see Realtek SDK vulnerabilities being exploited in the wild with over 10,000+ average IPS detections per month to deploy and distribute Denial-of-service botnet malware such as new Hinata Botnet, RedGoBot, GooberBot and Marai based Botnet.
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |