Android/Armour.A!tr
 Analysis
Analysis
Android/Armour.A!tr is a piece of malware targetting Android mobile phones.
The malicious package is a Fake Anti-Virus application that shows fake infections on the victim's phone and asks the user to enter Credit Card details in order to purchase the full version of the product so the phone can be 'Deep Scanned'. The user is charged 0.99 euros per day for the purchase of this rogue Anti-Virus.
The main application is called "Armour For Android"(ref Fig1) and comes in the package "com.armorforandroid.security"
![]()
Fig1 : Armour For Android Icon
When the application is launched, the user sees a screen as seen in Fig2.
The application contains no legitimate scanning functions.
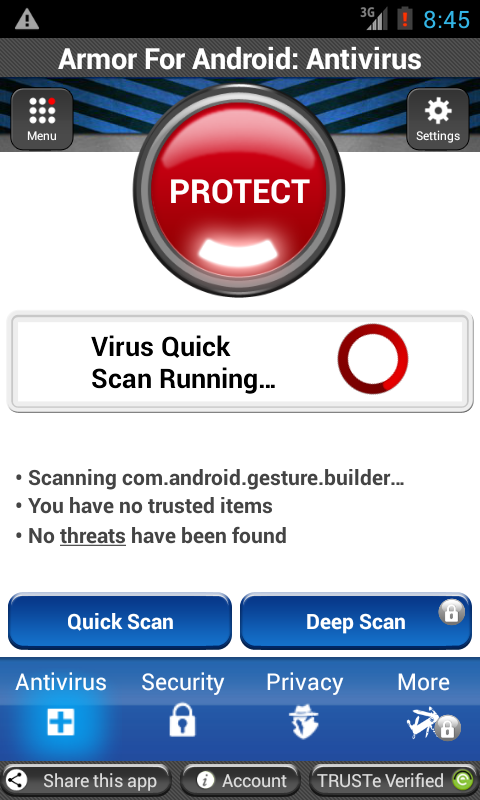
Fig2 : The application's Main Screen
Instead, when the user clicks on 'Quick Scan', an HTTP POST request is sent to
hxxp://scan.armorforandroid.com/quickwith the parameters
- "id" = [Code generated by manipulation of the ID described below]
- "json" = [Comma separated MD5 hashes of few packages on the phone]
The phone is not scanned instead the fake infections to be shown to the user are obtained by sending a request to
hxxp://antivirus.trafficmanager.net/check?a=[SEC_KEY]&id=[ID]&hash=[HASH]&package=[PKG]&system=truewhere
- SEC_KEY = Value of parameter "security_key" found in the package assets
- ID = MD5 Hash of a string that is generated using the phone's IMEI, Android ID and several other values from the phone's Android Build
- HASH = SHA1 Hash of ApplicationInfo.publicSourceDir
- PKG = Package Name
If the user chooses to perform a 'Deep Scan' on the phone, the application contacts the URL
https://www.appbuy.com/buy?pid=4that returns a payment screen as seen in Fig3.
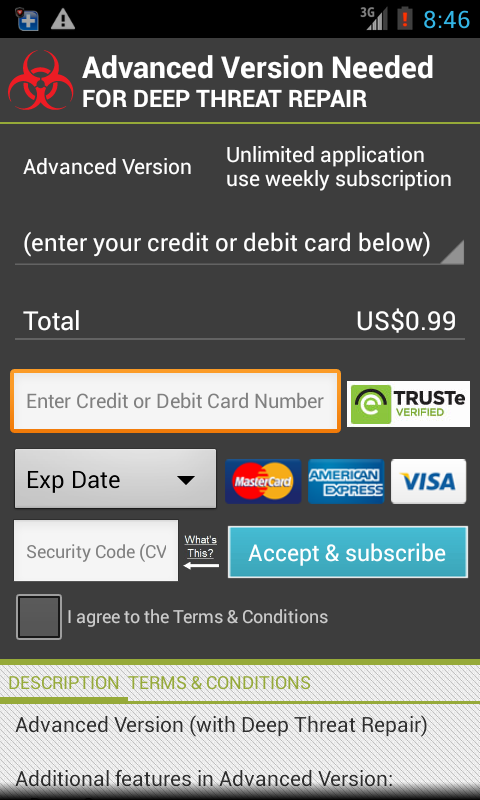
Fig3 : Payment Screen
If the user enters the Credit Card details requested, they are sent to
hxxps://cc.[REMOVED]report.net:8443/api.phpwith the parameters
- "configuration_history_id" = [Id obtained from the file upgrade.json in the package assets]
- "account_number" = [ID value - as explained further above]
- "product" = [Value of "vertical_short" obtained from the file upgrade.json in the package assets
- "package" = [Package Name]
- "cc_type" = ["VISA"/"MC"/"DISC"/"AMEX"/"UNK" depending upon the Credit Card Type entered by the user]
- "cc" = [Credit Card Number entered by user]
- "exp_month" = [Credit Card Expiry month entered by user]
- "exp_year" = [Credit Card Expiry year entered by user]
- "cvv" = [CVV Number entered by user]
Permissions required by the application:
- INTERNET
- ACCESS_NETWORK_STATE
- READ_PHONE_STATE
- ACCESS_WIFI_STATE
- READ_HISTORY_BOOKMARKS
- WRITE_HISTORY_BOOKMARKS
- KILL_BACKGROUND_PROCESSES
- RESTART_PACKAGES
- GET_PACKAGE_SIZE
- GET_TASKS
- CLEAR_APP_CACHE
- READ_CONTACTS
- WRITE_CONTACTS
- READ_SMS
- WRITE_SMS
- RECEIVE_BOOT_COMPLETED
- VIBRATE
- WAKE_LOCK
- WRITE_EXTERNAL_STORAGE
- READ_LOGS
- com.google.android.c2dm.permission.RECEIVE
- GET_ACCOUNTS
Certificate information:
- Owner: OU=Android Armour, L=Blah, C=ZZ
- Issuer: OU=Android Armour, L=Blah, C=ZZ
- Serial number: 5004ae0e
- Valid from: Tue Jul 17 02:13:02 CEST 2012 until: Sun Jul 07 02:13:02 CEST 2052
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| Extreme | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |
Version Updates
| Date | Version | Detail |
|---|---|---|
| 2019-04-12 | 67.75300 |