W32/Filecoder_cl0p.A!tr.ransom
 Analysis
Analysis
W32/Filecoder_cl0p.A!tr.ransom is a generic detection for a trojan.
Since this is a generic detection, malware that are detected as W32/Filecoder_cl0p.A!tr.ransom may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware is associated with the Cl0p ransomware family.
- Upon execution, this ransomware will traverse through the victim's system to encrypt the user's data. The encrypted files will have the extension ".C_I_0P" appended to the file name. A ransom note with the name "!_READ_ME.RTF" will be dropped in every directory that contains encrypted files. The ransom note will direct the user to contact the attacker via email/chat or risk having the data published to the public on the attacker's portal. Affected users are discouraged on taking this action as it does not guarantee the retrieval of data upon payment.
- Below are images of the ransomware:
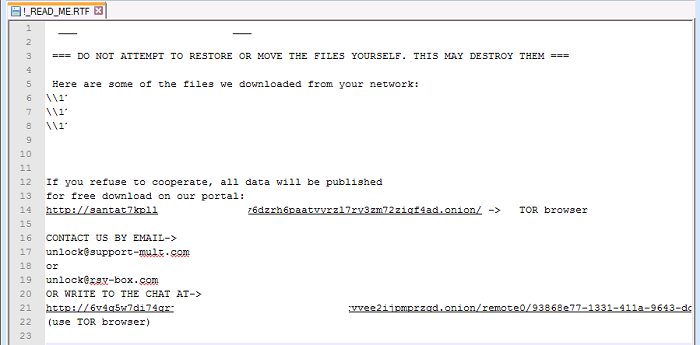
- Figure 1: Ransom note.
- Below are some of the sites associated with the trojan:
- http://santat7kpll[removed]y3zm72zigf4ad.onion/
- http://6v4q5w7di74grj[removed]rvvee2ijpmprzqd.onion/remote0/93868e77-1331-411a-9643-dc9a[removed]
- Following are some of the exact IOCs/file hashes associated with this detection:
- Md5: 4431b6302b7d5b1098a61469bdfca982
Sha256: dd2f458a29b666bbfe5a5dbf6a36c906d0140e0ae15b599e8b4da1863e7e41ff - Md5: 5e52f75d17c80dd104ce0da05fdfc362
Sha256: c793a9225d799150538f058c886e2806083f6bc33813a3bd8231ab2775b7ec2f - Md5: 8bd774fbc6f846992abda69ddabc3fb7
Sha256: a9741b16f4169f56ae0f2e49c87f3c5360ed5ab4370e6d16bd86179999f11795 - Md5: afe7f87478ba6dfca15839f958e9b2ef
Sha256: f1b8c7b2d20040f1dd9728de9808925fdcf035a1a289d42f63e5faa967f50664 - Md5: f59d2a3c925f331aae7437dd7ac1a7c8
Sha256: 46cd508b7e77bb2c1d47f7fef0042a13c516f8163f9373ef9dfac180131c65ed
- Md5: 4431b6302b7d5b1098a61469bdfca982
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |