W32/FilecoderPhobos.E!tr.ransom
 Analysis
Analysis
W32/FilecoderPhobos.E!tr.ransom is a generic detection for a trojan.
Since this is a generic detection, malware that are detected as W32/FilecoderPhobos.E!tr.ransom may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware is associated with the Phobos ransomware family.
- Upon execution, a GUI will be displayed. No files will be encrypted until the GUI is utilized. Depending on which option is selected from the GUI, the ransomware can encrypt the whole system, a selected folder, or the current directory of the malware.
- The ransomware will first delete shadow copies and backup catalogs before continuing on to encrypt the victim's files, excluding .exe and .dll files. The GUI will display the number of encrypted files. The encrypted file names will be appended with the Phobos variant name. The appended extension will be in the pattern of: id[victim_id].[email_address].[variant_name]. Some variant names include: ".makop" and ".mkp".
- A ransom note will be dropped to the desktop and to any directory containing encrypted files. Depending on the variant, the ransom note may be named "readme-warning.txt" or "+README-WARNING+.txt". The note will ask for payment and instruct the victim to make contact with the attacker via email. Decryption for a few files will be offered as a guarantee. Affected users are discouraged on taking this action as it does not guarantee the retrieval of data upon payment. Variants that drop "+README-WARNING+.txt", will also change the victim's desktop wallpaper to display a message stating that their files have been encrypted.
- Below are images of the result of executing the ransomware:
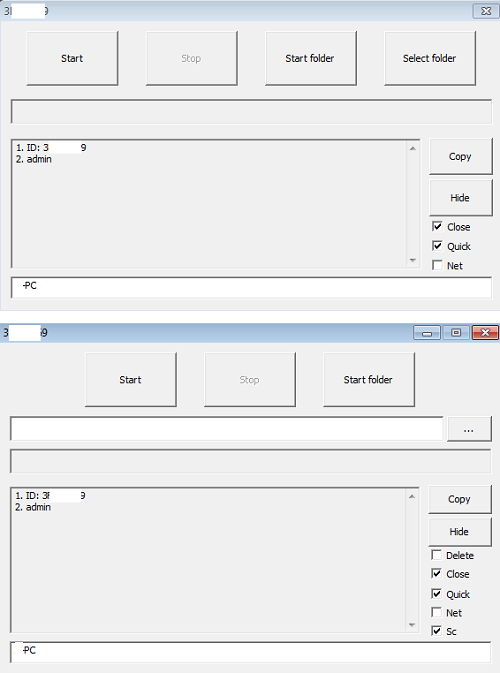
- Figure 1: Variations of the GUI.
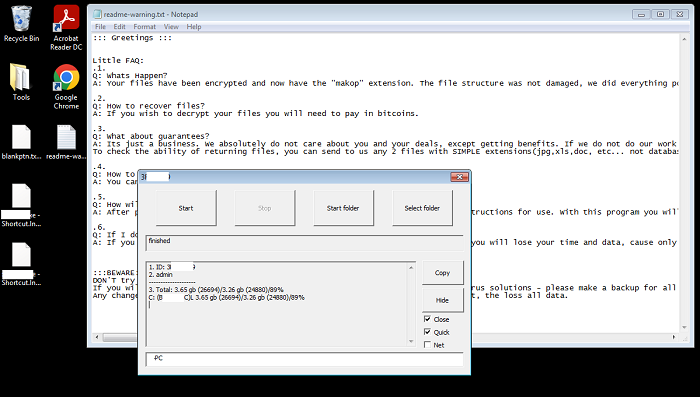
- Figure 2: Desktop with "readme-warning.txt".
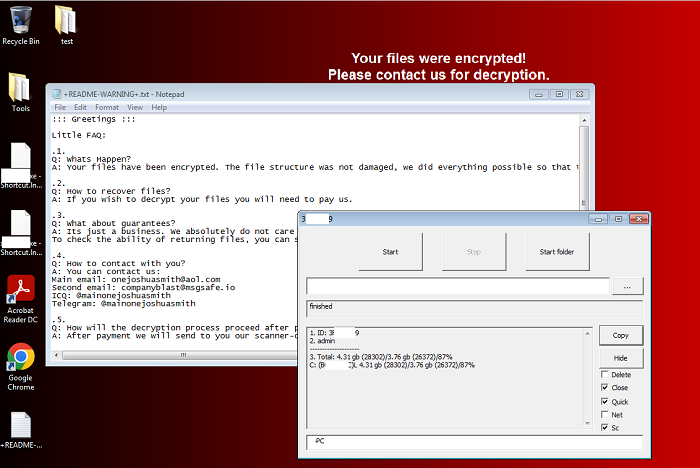
- Figure 3: Desktop with "+README-WARNING+.txt".
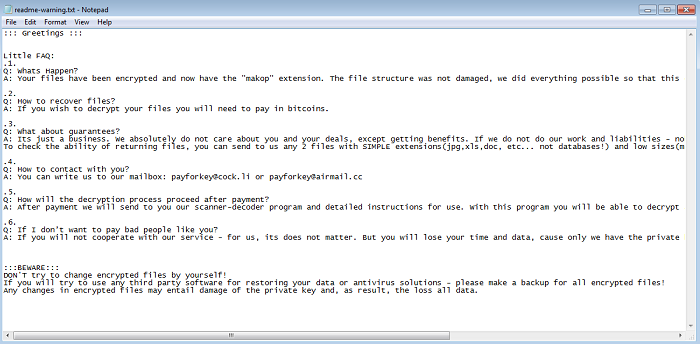
- Figure 4: Ransom note.
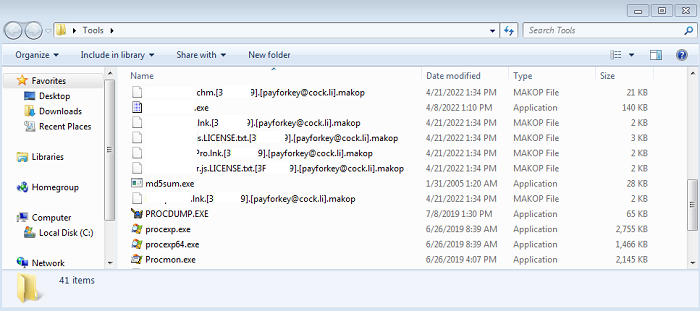
- Figure 5: Encrypted files (excluding .exe and .dll files).
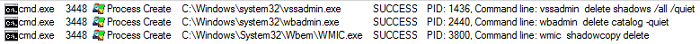
- Figure 6: Delete shadow copies and backup catalogs.
- Following are some of the exact file hashes associated with this detection:
- Md5: 00f0d40002671bff56c66d130891a81f
Sha256: 1d8876cdd7804d7638c26e653a21157efddfb793415f1ba1d2c2bf19937713a7 - Md5: 2be52da4a1890fa0ac227de1fe07505b
Sha256: 74446bd2905a27530f8cecb142fbfa9d921699db984a2bdc961746733367c49b - Md5: 2f26ab653fe7c323188be92fafe74bbc
Sha256: 85739f8bf1e084ea7b23c03821e287a8cfc9cda3e9ad15e37f4ca9fbcd34e099 - Md5: 82fb2d58d58120d6b9d129f8e3857e07
Sha256: 854226fc4f5388d40cd9e7312797dd63739444d69a67e4126ef60817fa6972ad - Md5: af5a70fb2c8fe97a8dc10b9fe585d9e6
Sha256: df01d6d33ae59766d17fca530c2554c29607b444f2ea3da9f462585b7c51ce79
- Md5: 00f0d40002671bff56c66d130891a81f
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |