NSIS/Injector.AOW!tr
 Analysis
Analysis
NSIS/Injector.AOW!tr is a generic detection for a trojan.
Since this is a generic detection, malware that are detected as NSIS/Injector.AOW!tr may have varying behaviour.
Below are some of its observed characteristics/behaviours:
- This malware is spread to unsuspecting victims via a NSIS file.
- This malware has been observed to harbor suspicious codes through which it creates a .dat file and allocates memory by calling VirtualAlloc. After which, it will read the .dat file into the buffer of the allocated memory. It then performs operations to find the decryption key needed to decrypt the payload before finally executing the decrypted code.
- After execution, the malware will inject itself into an executable and attempt to create an autorun registry for persistence. It will call Caspol.exe from the .net framework 4.0 to possibly try to modify security policies. Both the injected process and caspol.exe will continue to run in the background of the user's system for a period of time before finally exiting.
- Though in some cases where the NSIS package/installer itself carries within a none malicious application/contents, the suspicious behaviour mentioned earlier is considered a none common behaviour or none normal behaviour among enterprise/commercially available packers/installers, and thus would be open to being exploited by malicious attackers who intend to distribute their malicious binaries/payload thru this NSIS packaging bundle along with clean/normal apps. Users are always advised to obtain their apps via the official publishers/websites/sources of the app itself.
- Below are images of the malware:
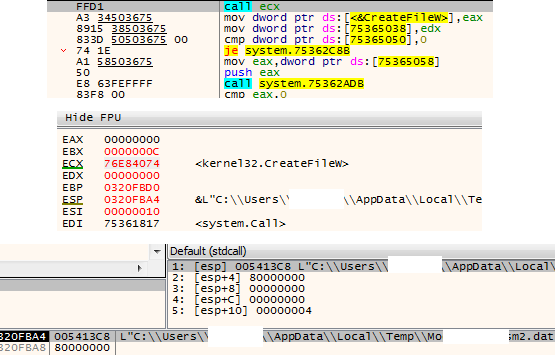
- Figure 1: Creating .dat file.
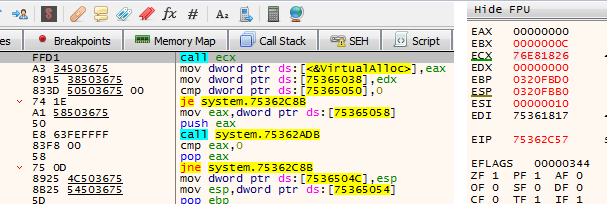
- Figure 2: Allocating Memory.
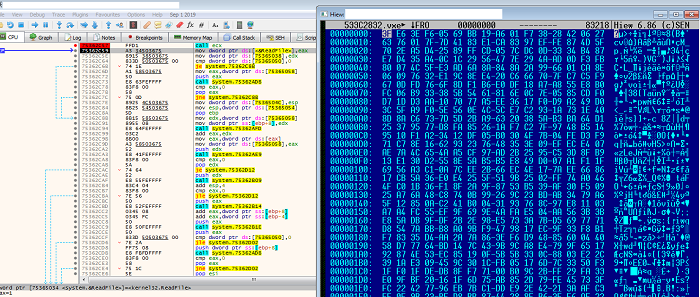
- Figure 3: File read into buffer.
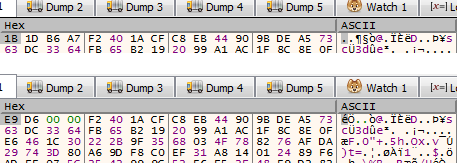
- Figure 4: Before and after decryption.
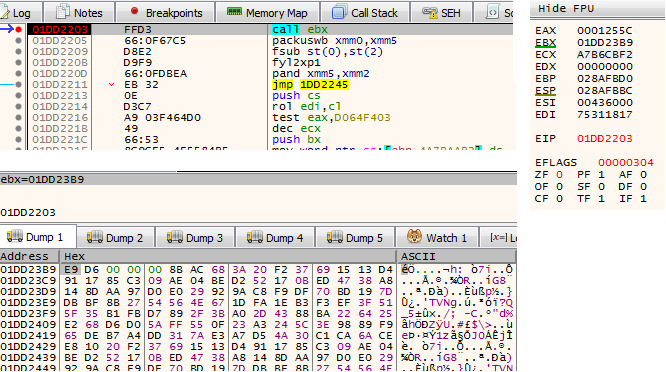
- Figure 5: Executing decrypted code.
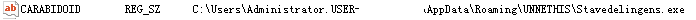
- Figure 6: Path of injected process.
- Following are some of the near/exact IOCs/file hash associated with this detection:
- Md5:0a169c6fa4c4af9f6d158e6d13b7573b
Sha256:e3a7dddeffaf52026cd3ac1858014ad7dbe458c45645d638e242f4e2e3622887 - Md5:72c7be61cfcf2c3be9d749bcbc35d761
Sha256:4022019919a0eca82becfb5c684be8c37d0c2c7b8f49a7f05ab93ccce8211d44 - Md5:82cc5dd67d9725f2c7fe6cd2a69c0219
Sha256:244eb8b4123fa7dce60daecf2f59306aa729ca409f238f52eb918786c05c919c - Md5:f735c92a5ed855d900216dc9f1710cab
Sha256:785ac73eb0e5ad5464b7e39e1a57c04bace72377e4aeac27452b4514d3d3dbec
- Md5:0a169c6fa4c4af9f6d158e6d13b7573b
 Recommended Action
Recommended Action
- Make sure that your FortiGate/FortiClient system is using the latest AV database.
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| FortiClient | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| FortiSandbox | |
| FortiWeb | |
| Web Application Firewall | |
| FortiIsolator | |
| FortiDeceptor | |
| FortiEDR |