Android/SMSZombie.B!tr
 Analysis
Analysis
Android/SMSZombie.B!tr is a piece of malware targetting Android mobile phones.
The malicious package sends out SMS messages from the victim's phone. It also deletes phone logs, monitors incoming SMS messages on the phone and selectively hides messages from the victim.
The trojan is difficult to uninstall, a software reset of the phone is often required to remove it.
Technical Details
The application is called "Android System Services" (in Chinese) (refer Fig1) and comes with package named 'android.phone.com'. Note the package's name is intentionally close to com.android.phone, a genuine Android application.
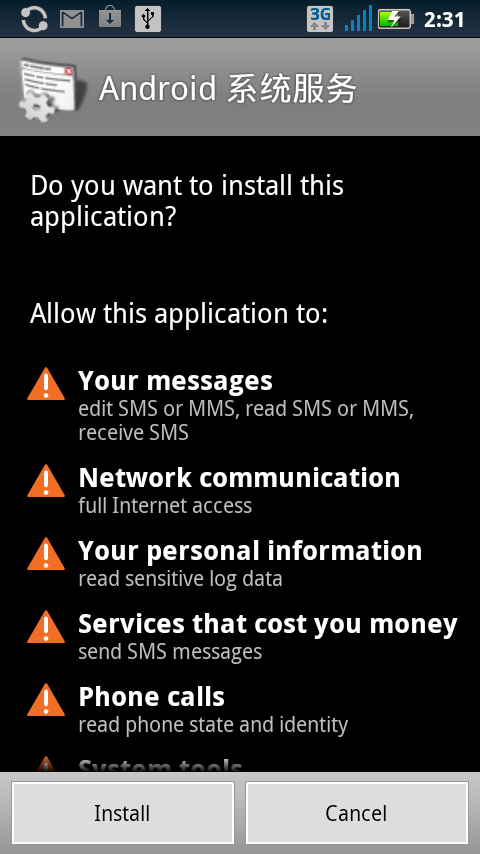
Fig1 : Malicious package installation
The malicious package details are as follows : The malicious application can't be seen in the main applications menu but can be seen in the list of installed applications in the Settings menu (refer Fig2)

Fig2 : Malicious package installed as seen in Settings menu Once installed, it launches the AndphoneActivity activity. This activity performs the following functions:
- Checks if the phone network type is 3G. If yes, it sends out an SMS message from the victim's phone to the number 1309xxxx with contents:
"1.5V:Model" + Build.MODEL + ";os" + Build.VERSION.RELEASE + ";Language" + lang + ";NET" + "3G"
Where Build.MODEL = phone model name, Build.VERSION.RELEASE = Android OS version number, lang = Phone language - If the phone network type is Wifi, it sends out an SMS message to 13093632006 with the message "The program runs again"
- Launches the anphone activity
- Launches the service TService
- Creates the file "/data/data/android.phone.com/files/phone.xml" that is used by the SMSReceiver as described further below
Date + ":" + Originating address of SMS received + "--" + contents of SMS receivedwhere the date is in the format "yyyy-MM-dd HH:mm:ss"
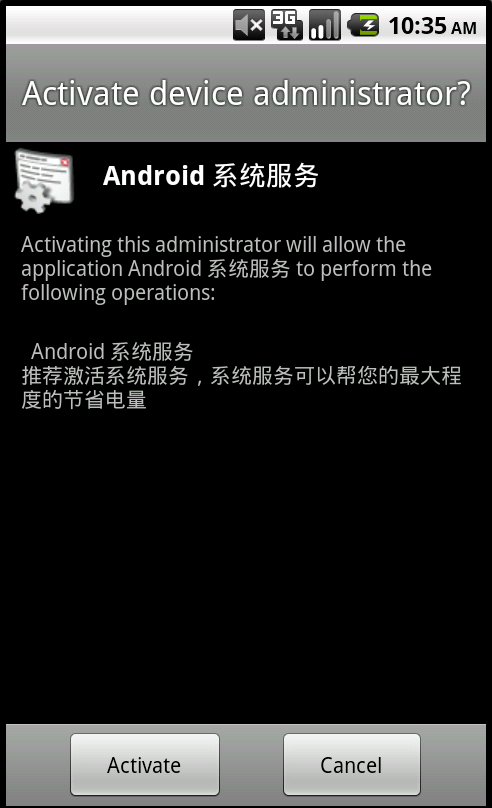
Fig3 : Device Administration Receiver Activation. The message in Chinese roughly translates to 'System services that help save power'
- mService prevents the trojan from being uninstalled on the phone by redirecting the user to the main applications menu upon attempting uninstallation. In order to uninstall the trojan, the victim must either deactivate the application's device admin receiver before uninstallation or perform a software of the phone. It also deletes logs from the phone using the command "logcat -c"
It then sends out an SMS message to 13093632006 with the contents "Has been activated, NOroot" (if the phone is not rooted) or "Has been activated, Already root" (if the device is rooted).
Permissions required by the application:
- RECEIVE_BOOT_COMPLETED
- RECEIVE_SMS
- SEND_SMS
- READ_SMS
- WRITE_SMS
- INTERNET
- ACCESS_NETWORK_STATE
- READ_PHONE_STATE
- ACCESS_WIFI_STATE
- READ_LOGS
- KILL_BACKGROUND_PROCESSES
- RESTART_PACKAGES
- GET_TASKS
Mainly aimed at Chinese users
Certificate information :
- Owner: CN=Android Debug, O=Android, C=US
- Issuer: CN=Android Debug, O=Android, C=US
- Serial number: 4ffbd058
- Valid from: Tue Jul 10 08:48:56 CEST 2012 until: Thu Jul 03 08:48:56 CEST 2042
- Certificate fingerprints:
- MD5: EF:54:0B:2E:4B:DD:53:83:AC:72:EB:AD:DA:D9:94:5E
- SHA1: 5B:8F:3D:74:27:B3:34:BC:30:B5:8B:AA:84:1D:F3:C8:7B:BE:5D:C2
- Signature algorithm name: SHA1withRSA
- Version: 3
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extreme | |
| FortiClient | |
| Extended | |
| FortiMail | |
| Extended | |
| FortiSandbox | |
| Extended | |
| FortiWeb | |
| Extended | |
| Web Application Firewall | |
| Extended | |
| FortiIsolator | |
| Extended | |
| FortiDeceptor | |
| Extended | |
| FortiEDR |