Android/FakeNotify.A!tr.dial
 Analysis
Analysis
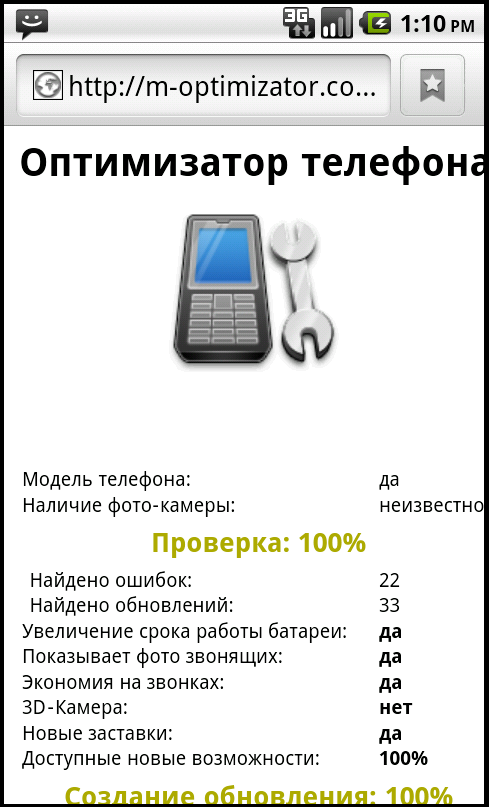
Android/FakeNotify.A!tr.dial is typically downloaded from a web site on which it is advertised as a phone optimizer for Android that reveals hidden capabilities of the phone.
|
|
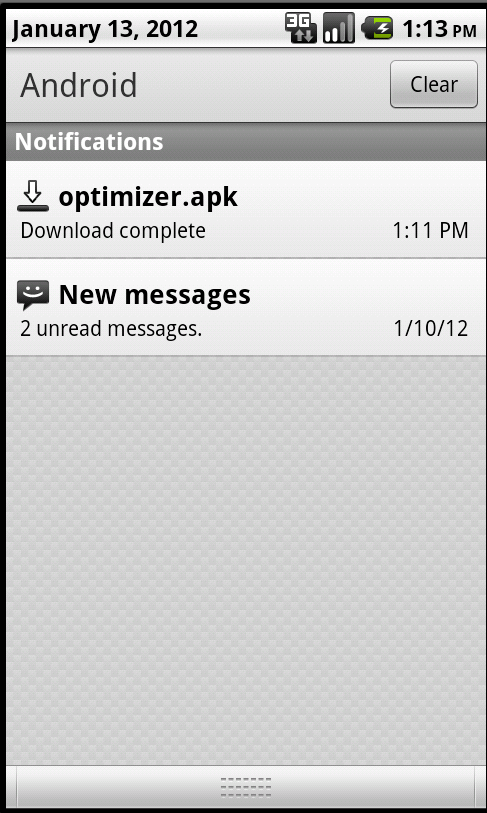
| Figure 1. Web site advertising phone optimizer | Figure 2. The Android malware is downloaded when visiting the page with an Android phone |
|
|
|
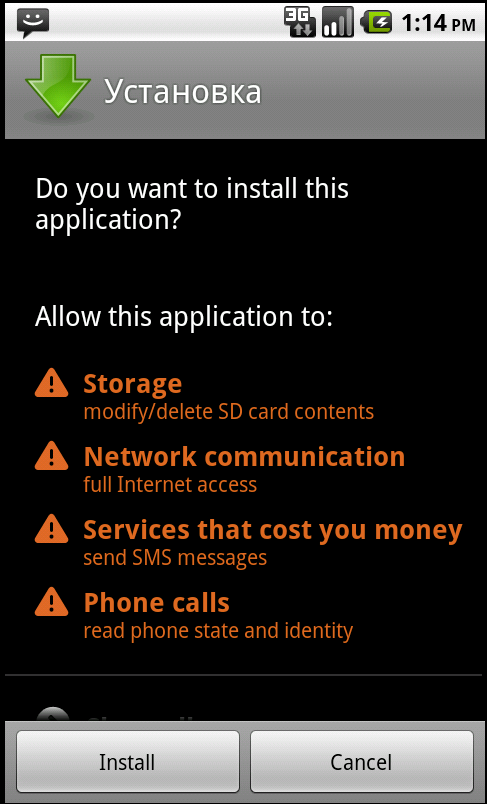
| Figure 3. Malware is installed on the phone | Figure 4. Permissions requested by the malware |
Technical Details
Android/FakeNotify.A!tr.dial is the Android version of Java/FakeNotify.A!tr.dial.
It is malicious in two ways:
- It send SMS messages even before the victim has the change to read and accept the license terms.
- and it is downloaded on a 'phone optimizer' web site, intentionally deceiving the end-user.
- the settings are stored in a raw database file located in res/raw/data.db
- the malware uses character substitution to obfuscate parameter names
 Recommended Action
Recommended Action
- FortiGate Systems
- Check the main screen using the web interface for your FortiGate unit to ensure that the latest AV/NIDS database has been downloaded and installed on your system - if required, enable the "Allow Push Update" option.
FortiClient Systems
- Quarantine/delete files that are detected and replace infected files with clean backup copies.
 Telemetry
Telemetry
Detection Availability
| FortiGate | |
|---|---|
| Extended | |
| FortiClient | |
| Extreme | |
| FortiAPS | |
| FortiAPU | |
| FortiMail | |
| Extreme | |
| FortiSandbox | |
| Extreme | |
| FortiWeb | |
| Extreme | |
| Web Application Firewall | |
| Extreme | |
| FortiIsolator | |
| Extreme | |
| FortiDeceptor | |
| Extreme | |
| FortiEDR |